Overview
Wormhole would like to propose to the Rocket Pool DAO integrating rETH with Native Token Transfers. Through NTT, Rocket Pool will be able improve cross-chain user experience, unlock additional growth opportunities, and reduce bridge liquidity cost. By integrating with NTT, the Rocket Pool DAO will future proof itself with cross-chain flexibility for rETH, gaining access to all current and future networks that Wormhole connects to.
What is Wormhole
Wormhole is an industry leading interoperability protocol that allows for message passing between blockchain networks. Since inception, Wormhole has processed over a billion messages, processing over $46B in total volume. Wormhole enables builders and protocols across the full-stack of interoperability. For example, Circle worked directly with Wormhole to design their Cross Chain Token Protocol, which Wormhole has supported over $500M in total volume on to date.
Wormhole messaging protocol consists of both onchain and offchain components. These components help to verify and communicate messages across networks. To learn more about the general architecture please visit the wormhole website!
Guardians
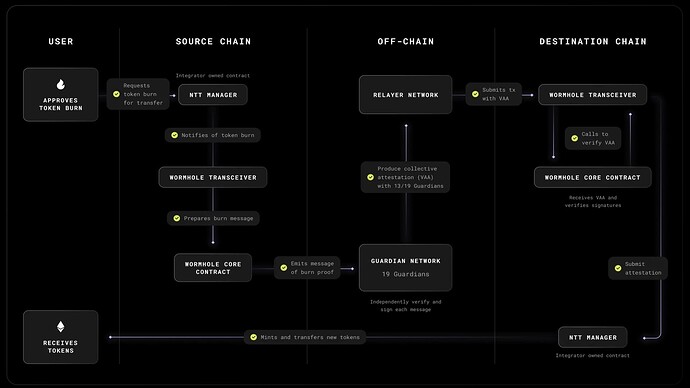
Wormhole relies upon a set of distributed nodes which monitor state on several blockchains. In Wormhole these nodes are referred to as Guardians. The current guardian set can be seen in the Dashboard.
It is the guardians role to observe messages and sign the corresponding payloads. Each guardian performs this step in isolation, later combining the resulting signatures with other guardians as a final step. The resulting collection of independent observations form a multisig which represents a proof that a state has been observed and agreed upon by a majority of the wormhole network. These multisigs are referred to as VAAs in Wormhole.
Decentralization
Guardians
Decentralization is one of the biggest concerns when it comes to interoperability. Previous interoperability solutions have largely been entirely centralized, and even newer solutions utilizing things like adversarial relayers still tend to have single points of failure or collusion thresholds as low as 1 or 2.
Wormhole’s approach to message validation was to initially secure the network by involving robust companies which are heavily invested in the success of De-Fi as a whole, rather than securing the network with tokenomics. The 19 Guardians are not anonymous or small–they are many of the largest and most widely-known validator companies in cryptocurrency.
Each Guardian has an equal stake and joined in a purpose-built Proof of Authority consensus mechanism. As threshold signatures become better supported, the Guardian set can expand, and once ZKPs are ubiquitous, the Guardian Network will become fully trustless.
DAO
Wormhole is committed to further decentralization through token governance of the protocol. In accordance with this stance, Wormhole is in the process of setting up DAO governance. The first step to this process has begun, where W token holders are able to stake and delegate their holdings to participate in governance.
To help the structure and to legitimize the process, Wormhole is partnering with several entities known in the space for DAO governance such as GFXLabs, 404Gov, and L2BEAT.
You can access the forum via adding ‘forum.’ to the official wormhole website address. (limited by Rocket Pool forum posting)
Future State
Wormhole’s ethos is aligned with Rocket Pool’s. Wormhole code is entirely open-source and primary services, such as NTT, are permissionless. Wormhole is thoroughly committed to pursuing continued decentralization, empowering token holders to help shape the future of the protocol.
External Assessment
A testament to the robust, trust-minimized design of Wormhole, Uniswap DAO chose Wormhole as the partner for executing the deployment of Uniswap v3 across L2 networks. The committee that assessed various bridge providers based on the following framework.
- Protocol Architecture Risk: Encompasses the risks stemming from the design of a protocol, including its primary validation mechanism and other architecturally significant components that impact the fundamental security properties, assumptions, and trust model associated with the protocol.
- Protocol Implementation Risk: Includes the risks associated with the implementation of a protocol’s specification. Building cross-chain protocols involves creating complex on-chain and off-chain components while accounting for the peculiarities and pitfalls of different programming languages, frameworks, and execution environments.
- Protocol Operational Risk: Refers to the various risks that arise from the operational security and management of different components, often by different actors with different trust assumptions and incentives. This could include upgrading and managing bridge smart contracts, as well as operating off-chain systems such as external validator nodes.
- Network Risks: Cross-chain protocols rely on certain assumptions about the safety and liveness guarantees of underlying networks. Consequently, these protocols have fundamental limitations in the guarantees they can offer. This category of risk encompasses how cross-chain protocols handle violations to these assumptions in any given network and mitigate the impact on other connected networks and application
The full Uniswap DAO Bridge Assessment Report can be found here.
Native Token Transfer
Wormhole’s Native Token Transfers (NTT) is an open source, flexible, and composable framework for transferring tokens across blockchains. Integrators have full control over how their tokens that use NTT behave on each chain, including the token standard, metadata, ownership, upgradeability, and custom features.
Current rETH Landscape
rETH is currently live on Optimism, Arbitrum, Base, and Polygon outside of mainnet. Rocket Pool had previously assessed interoperability providers and ended up deciding on just leveraging canonical bridges for L2 deployments. Outside of canonical bridges, Rocket Pool is currently funding liquidity pools for Optimism and Arbitrum.
rETH’s presence on Layer 2’s varies. As seen in the Layer 2 vibe check forum post, participants in Rocket Pool governance have a divided view of value for each chain. Protocols such as Aave and Eigenlayer have created strong demand for rETH. It is expected that with the advent of any-asset restaking and new protocols with fresh token supplies, rETH will have a source of demand. Proliferating rETH into ecosystems such as Scroll, Linea, Monad, and other upcoming chains in combination with tapping into the aforementioned protocols will amplify rETH’s growth in DeFi.
Benefits of an NTT Integration
The Ethereum Foundation has made the roadmap for Ethereum roll-up centric. Also, with the advent of companies such as Conduit, it has never been easier to launch a new network. It is simply not feasible for Rocket Pool DAO to decide which L2 to focus their efforts on nor assess each bridge. Wormhole can reduce the overhead on the Rocket Pool DAO by enabling the launch of rETH with minimal effort. With NTT, the Rocket Pool DAO can seamless launch rETH across these chains with minimal effort and gain access to key ecosystems and protocols that will want a battle tested asset such as rETH. Lastly, Wormhole can help with growth efforts such as co-marketing, go-to-market strategies, day-1 bridging into upcoming chains, and more.
Key Benefits
- Unified User Experience: Tokens retain their properties on each chain, remaining completely fungible and ensuring a consistent user experience.
- No Liquidity Pools: Transfer tokens without the need for liquidity pools, avoiding fees, slippage, and MEV risk.
- Integrator Flexibility: Retained ownership, upgrade authority, and complete customizability over token contracts.
- Advanced Rate Limiting: Inbound and outbound rate limits are configurable per chain and over arbitrary time periods, preventing abuse while managing network congestion and allowing for controlled deployments to new chains.
- Global Accountant: Ensures accounting integrity across chains by checking that the number of tokens burned and transferred out of a chain never exceeds the number of tokens minted.
- Access Control: To prevent unauthorized calls to administrative functions, protocols can choose to assign certain functions, such as the pauser role, to a separate address from the owner.
- Maximum Composability: Open-source and extensible for widespread adoption and integration with other protocols.
- Custom Attestation: Optionally add external verifiers and configure custom message attestation thresholds.